We launched our very first hackathon event in October, IPinfo IP Hunt. With IPinfo reaching its 10th birthday last year, launching our free IP databases and launching our freshly updated app (iOS and Android app), we wanted an opportunity to personally say “Thank you” to the developers who have been using our API. We have been supporting developers worldwide with our accurate IP insights for years, and we wanted this event to truly celebrate what binds our entire developer community in one unifying idea: “IP Address”.
How did the idea come to be?
We wanted to do something special; we didn't want to do an event where users had to submit programming projects, technical content, or something. We wanted this event to truly celebrate the idea that IPinfo represents, and in the process, we hoped the developer community (as well as the IPinfo team) could learn something new.
The initial idea of the hunt was about people running around public WiFi hotspots to collect IP addresses. It was supposed to be like "Pokémon GO for IP Addresses." We thought people could grab a few WiFi IP addresses from carrier IP addresses, and then the majority of the IP addresses would be from coffee shops, schools, public libraries, etc. We also set up the mechanism so that users could use multiple devices and add the device IDs of their friends and family to their hunted IP addresses.
But, from the title, you probably figured that didn't turn out that way... let's keep going.
At the beginning of the ideation stage, we thought about announcing winners based exclusively on a leaderboard. However, after our test runs, we found that our colleagues from some regions had more access to public WiFi than others. So, we decided not to move forward with a top user-based challenge.
We opted to do a lottery/raffle-based prize. Each IP you collect for the day is considered a raffle token for the lottery. Even though collecting more IPs gives you a better chance to win, everyone can win something as long as they hunt IP addresses. Moreover, a winner can only win one type of item at a time, and we have multiple prize drops. But the idea of this being a challenging IP Hunt held.
Launch day ….. then it really took off
We finally launched the event on October 23, and things went smoothly. Participants were collecting IP addresses, and everyone was excited.
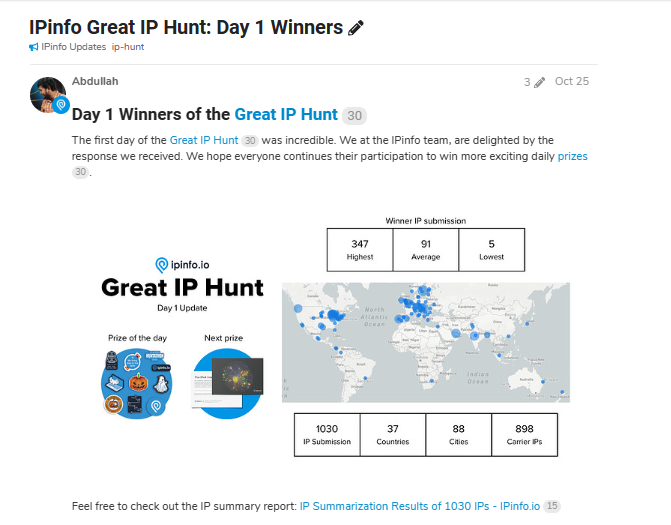
On our first day, we had our IPinfo sticker pack as a prize. We received about 1,030 IP submissions. The highest submission for a user was 347 and came from WhiteFireOCN. Even though the idea that a single user could submit (or connect) to hundreds of IP submissions was interesting, we were not concerned about it. We thought they were a very proactive user who had worked in an organization or a university with multiple WiFi hotspots. At that time, we didn't investigate individual user submissions.
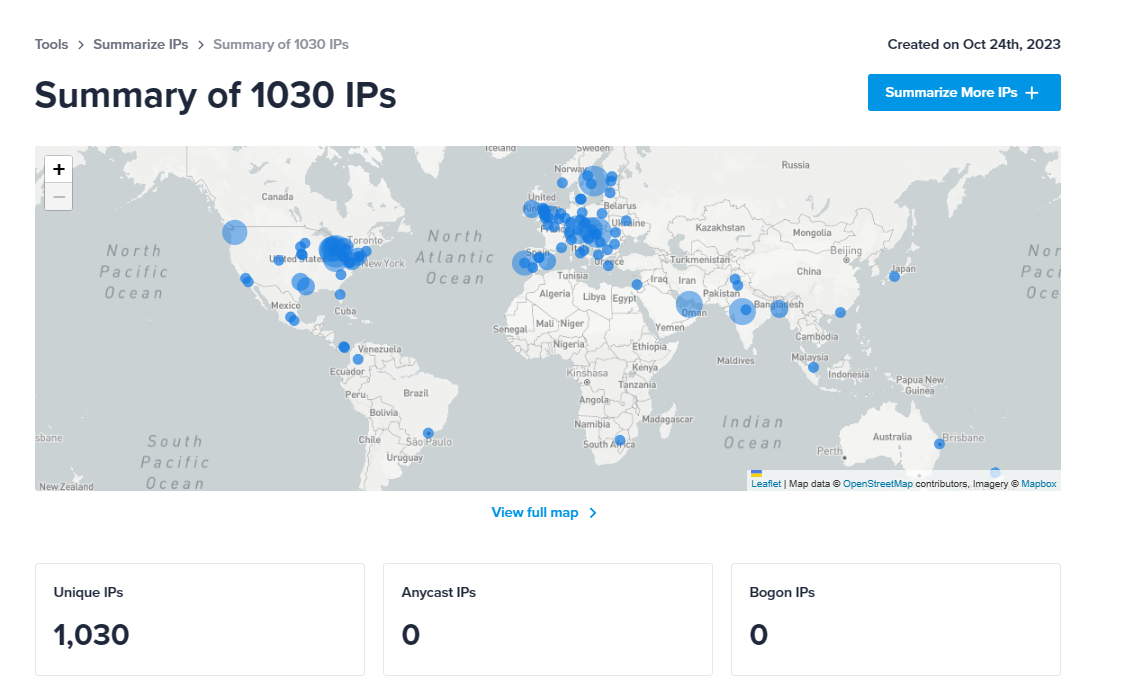
We announced our winners via our community and provided an IP summary of the results for the day using our online summary tool. The community posts and summary reports are still available in the community if you are interested in taking a look.
Users can also request their IP summaries of the collected IP addresses for the day through private messages. Our IP summary tool supports up to five hundred thousand (500,000) IPs and has an API endpoint for posting IPs. Therefore, it was quite easy for us to send IP summaries to individual users.
Then came the second day, and that is when we realized that the event would be something special. We started receiving many submissions, and we were fairly confused about what was going on.
The IP submissions are registered at the TCP connection level and extracted from our logs. There is no way for users to send IP addresses directly. They must first be connected to an IP address and then send a request to our servers from that IP. Only then will the IP be considered a submission.
Even though we knew that the top users at this moment had been able to successfully reverse engineer our app or find some level of loophole, the IPs they were submitting were legitimate in the sense that those IP addresses were used to request our web services.
Two types of patterns emerged:
- Large clusters of devices centrally located around a certain geolocation.
- Completely random and globally distributed devices.
But at this time, both of these types of users were leading the rankings and submitting more or less the same number of IP addresses even though there were thousands of IP addresses. We were sure the clustered devices were not residential proxy addresses, but the sheer volume of distributed IP submissions felt too big to be residential proxies. We had nothing but theories at that moment.
The next day, we realized that the clustered IP address submissions mainly had only one ASN, which is usually a carrier ASN. So, I will unravel the secrets later. We were confused and watched as the number soared and our IP count kept ticking up.
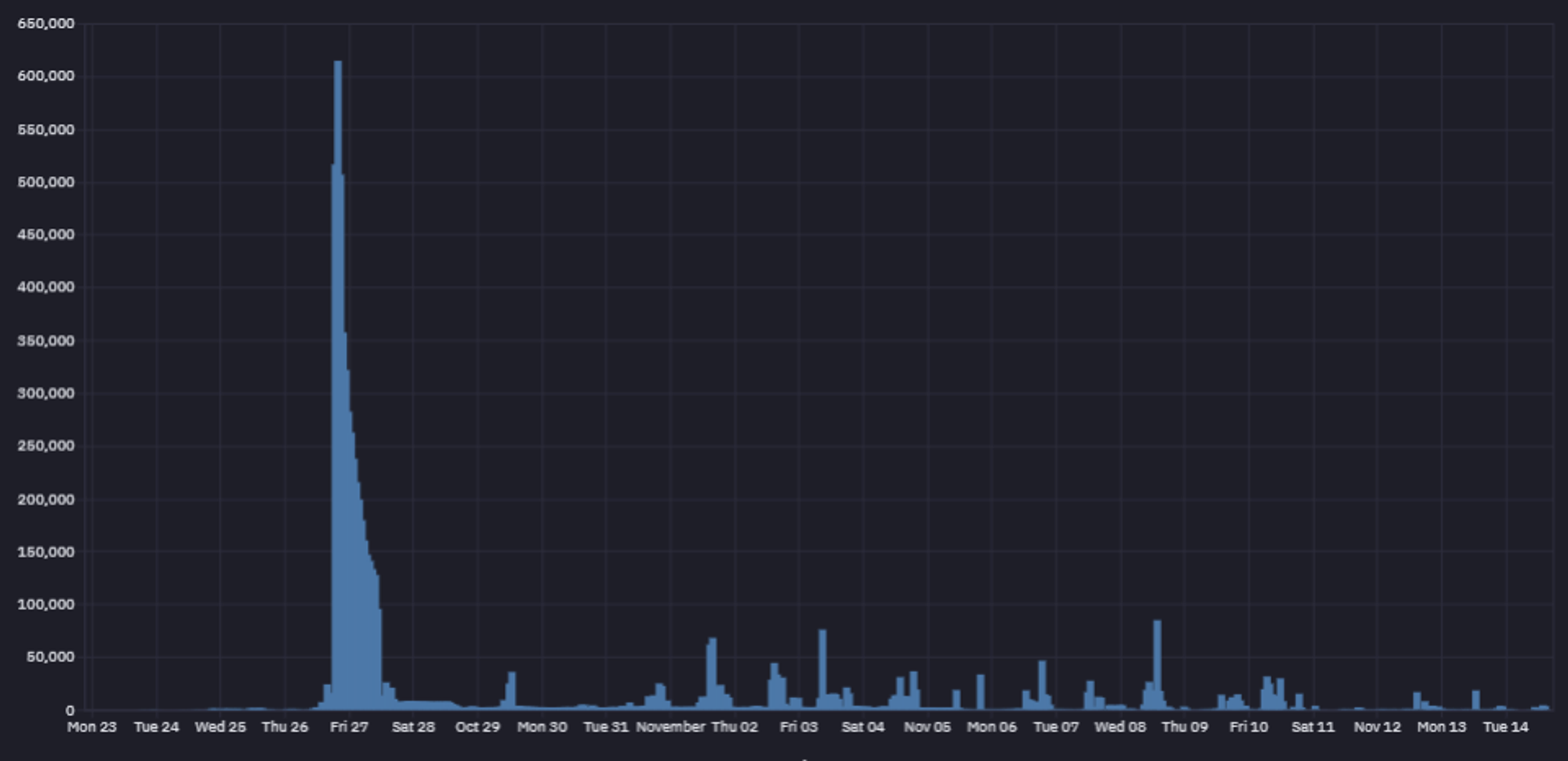
Then, on the 4th day, it finally happened – the total IP submission count exceeded 1.3 million IP addresses!
We still had no clue how only 244 users could submit 1.3 million IP addresses over 3-4 days.
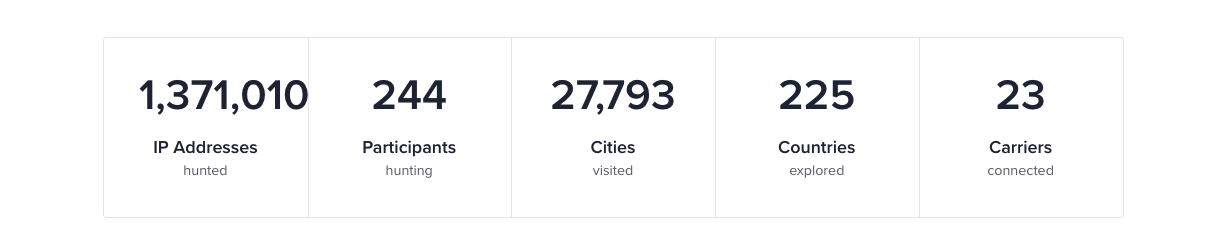
We were not prepared for this level of traffic for such a small event, as evidenced by the CSS overflow of the 1,371,010 submissions. Our backend services struggled a bit to show the accepted IP addresses. Since this is an experimental event for us, we did not allocate significant computational resources behind it, and the event was more or less halted. However, our engineer was able to jump to the task and make the event operational again.
While the event was slowly being revamped, we noticed that the group leader had submitted over nine hundred thousand (900,000) unique IP submissions. Surprisingly, 92.2% of those IPs came from ISP connections with no common ASNs.
And after that, we had a full-on discussion in our community with the participants, and everyone shared their recipes. It was truly one of the greatest moments of IPinfo's community.
IPinfo Great IP Hunt: Day 3 Winners - IPinfo Updates - IPinfo Community
Both the clustered device and the global device folks came to discuss the event.
Internally, though, we were confused about what should be done. Even though they were able to game the system, our CEO, Ben Dowling, essentially said, "we will take them all!" This level of IP submission was truly incredible, and even though we are an IP address database company, we were learning a ton here.
Progressively, people started to bring their friends and family to the event to win our merch, and we were excited by the momentum.
Extending the event
The initial runtime of the event was two weeks; however, since top-level users cannot win the same prize twice, they asked their friends, family, and acquaintances to join the event. As the new users were equally excited about the event and actively participated, we deemed it fair to extend the event by a week to allow them to win.
How the event went
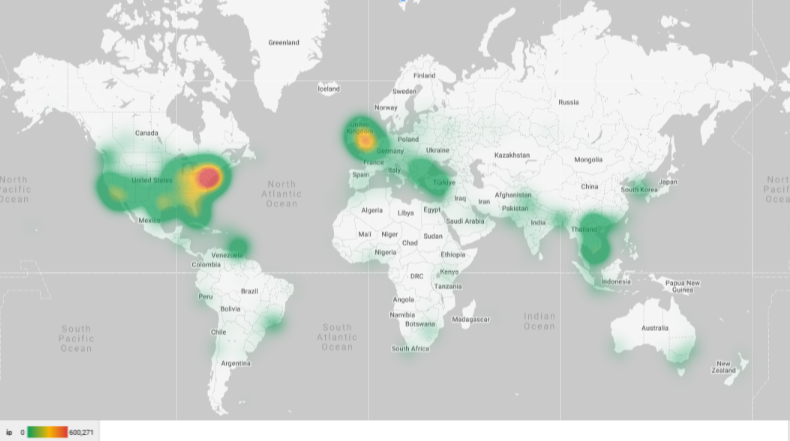
The total number of signups was 315 individual users. The total number of accepted IP addresses was 2.3 million IPs. These IP addresses spanned across thirty-four thousand (34,550) cities and two hundred (228) countries. We had about 70 winners, most of whom won multiple prizes through the lottery.
The day-to-day IP submission graph showed something really special happened on day 4 of the IP Hunt. All our top users aggressively hunted IP addresses while Rev.Pm and exove.ovh led the way.
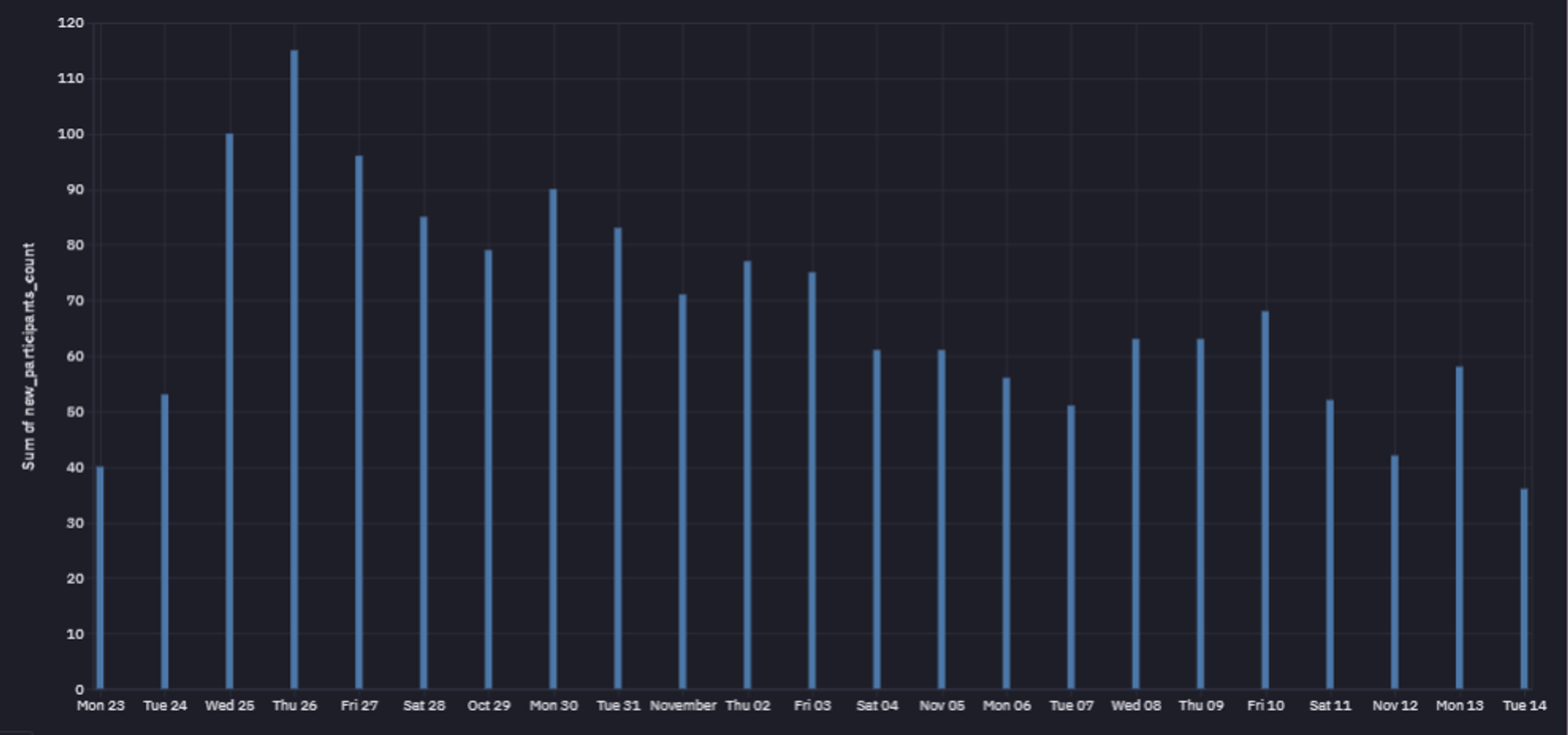
The following chart showcases the number of daily participating users. User participation was consistent throughout the event because most users brought their friends to the party after joining. Most users just enjoyed the hunt and participated to keep their position on the leaderboard.
The vast majority of the IP submissions came from users who were able to game our app.
Winning Strategy 1: Usage of a proxy network
| Rank | User | IP Submissions | Days Active |
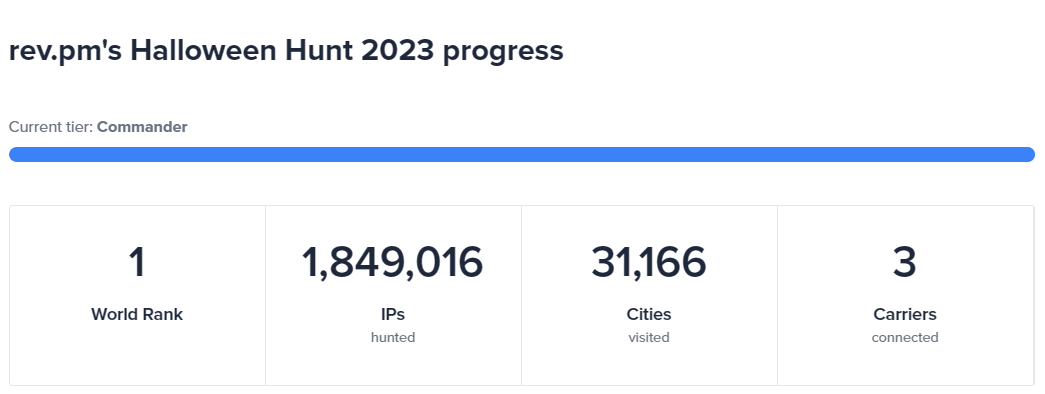
| 1 | rev.pm | 1849016 | 13 |
| 2 | quartz | 492335 | 11 |
| 3 | exove.ovh | 458818 | 9 |
| 4 | ismhdez | 354957 | 20 |
| 5 | samfces | 223046 | 9 |
| 6 | hibenji | 149853 | 9 |
| 7 | Luke | 108762 | 10 |
| 8 | hunt. | 95404 | 18 |
| 9 | Luc | 21955 | 9 |
| 10 | CLN.io | 18649 | 16 |
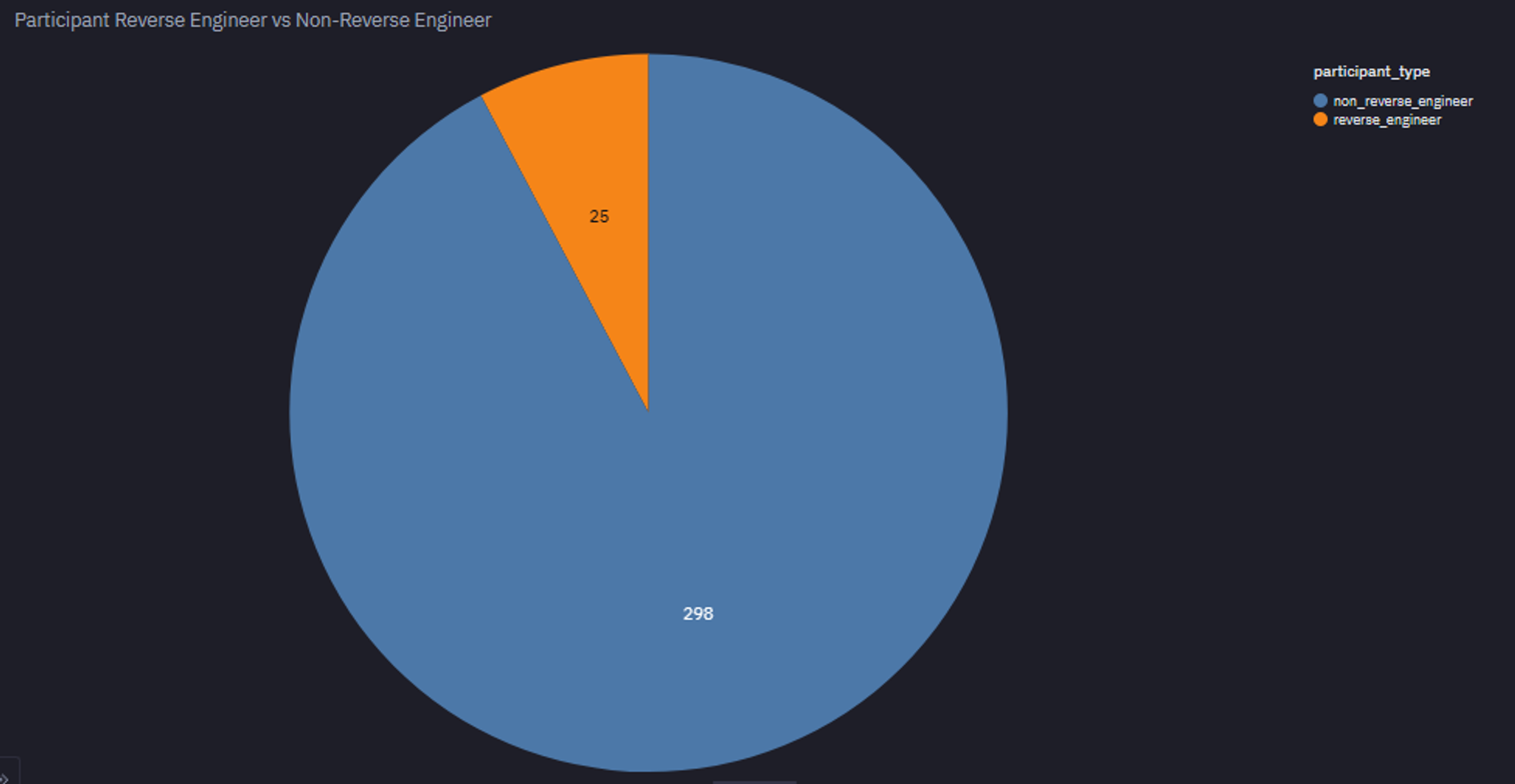
Every single user except for our #8 user (hunt.) and #10 user (CLN.io) used a residential proxy network strategy.
We talked with our top users who have adopted this strategy, but to maintain their secrecy, we prefer not to go into the details of the strategy. Essentially, these individuals downloaded an Android emulator, reverse-engineered our app to identify the API endpoint, and then started sending traffic to our site using a network of proxy devices. All of these individuals had two things in common: they had a cat profile picture in their community user profile, and they actually knew each other through online communities.
Fantastically, our Hibenji (#6) discussed his entire technical methodology of reverse engineering our app and using ProxyScrape, a residential service provider. We highly recommend giving the article on Proxyscrape’s website a read: How I used ProxyScrape proxies to win ipinfo.io merchandise.
When it comes to IP geolocation, there is no common pattern to it. This does showcase an important point about IP metadata. If you run threat intelligence operations, you must use multiple datasets to identify patterns.
| User | IP Countries | Leaderboard Rank |
| rev.pm | 228 | 1 |
| exove.ovh | 211 | 2 |
| quartz | 209 | 3 |
| ismhdez | 205 | 4 |
| samfces | 196 | 5 |
However, although they know each other when talking with them, we discovered that none of them actually shared their code with another person. They essentially came to the same conclusion using different methods.
Most of these users are also well-known in other communities with an equivalent "capture the flag" game where participants submit IP addresses. We were not aware of the existence of such communities, and we learned a lot from our users.
Despite some users raising concerns, we believe that everyone gained valuable knowledge from their participation, and the primary goal was to have fun. However, we acknowledge the need to strengthen the challenge in IP submission. As Piet Hein once said, "Problems worthy of attack prove their worth by fighting back." Please let us know if you have any suggestions for checks and roadblocks we can implement. We would be happy to incorporate them.
Winning Strategy 2: Carrier automation
For this, I would recommend reading our ranked #10 user [CLN.io]’s guide: Automating IP cycling on mobile networks for profit (a pair of socks) - CLN.io
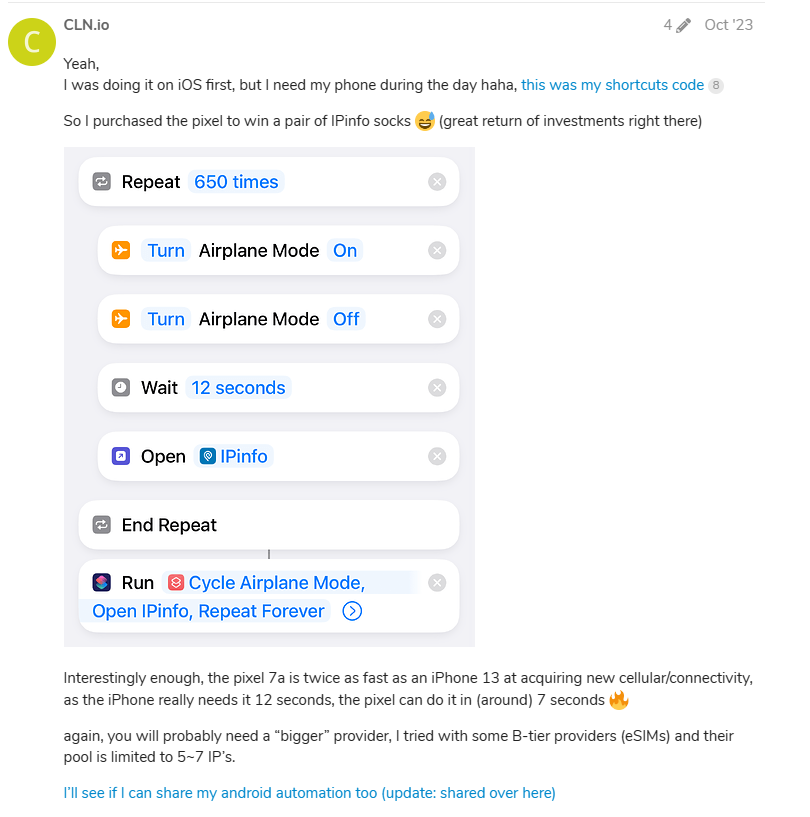
The strategy for this one is simple: constantly toggle flight mode on and off. Each time the user's carrier internet connection disconnects, they get assigned a new IP address from your carrier. Whenever they are assigned a new IP address, they will open up the app and wait a bit for the IP to register.
We were really surprised to see carrier IP churning like that, and we didn't realize that every time a user toggled their internet connection, a new IP address gets assigned. Another interesting fact is that we have seen multiple people independently discover this strategy.
Top users who had the IP countries limited to only 3
| User | Total Submissions | IP Countries | World Rank |
| hunt. | 95404 | 1 | #8 |
| CLN.io | 18649 | 3 | #10 |
| Elliot J | 10854 | 2 | #12 |
| Muse | 9477 | 2 | #14 |
| Person2099 | 5430 | 1 | #16 |
There were maybe 2-3 other methods that were used that took advantage of internet infrastructure or internet service organization access, but we have doubts but no evidence to show. ISPs may be able to relay internet traffic through a customer's router; however, we are unsure if this strategy was adopted. If you have such strategies to test out, join the event next time ;)
Winning Strategy 3: Being consistent throughout the event
This is probably not the most obvious strategy from the beginning: being consistent. The event was made for having fun, and if you have fun while submitting IP addresses at your own pace, you will eventually win a prize. Our prize rules were simple:
- Max five types of prizes for each contestant
- A contestant can only win one type of prize once
- Prizes are given away through a lottery
As the prizes are distributed through a lottery, everyone has a non-zero chance of winning something. Prizes are distributed based on IP submissions. So, the more IPs you submit, the higher your chances of winning; also, the more days you are active, the higher your chances of winning prizes! Shoutout to our most active users!
| User | Days Active |
| WhiteFireOCN | 23 |
| Remy | 22 |
| JamieT | 22 |
| Z87 | 22 |
| Johnnie | 21 |
Our winners

Top countries based on IP geolocation.
| Country Code | Total IPs Submitted |
| US | 1116452 |
| GB | 261273 |
| TW | 100625 |
| VN | 93310 |
| CA | 75124 |
https://community.ipinfo.io/t/the-great-ip-hunt-is-over/3906
We sent out a bunch of merch, and users were kind enough to share some pictures with us.

The response was overwhelmingly positive. Everyone who joined hung around in the community and really had a blast. Of the hundreds of participants, we were truly surprised by some participant metadata.
The classic term "customer persona" did not apply here, as we saw enterprise organization executives, consultants, OSS project maintainers, and even high school students join the hunt. People from the United States all the way to Japan, and from Russia to Australia, joined the hunt and shared the common joy of using IPinfo's services.
See you at the next IP Hunt
The success of the hackathon was enormous. It really meant something special for us and for the community. We would love to hear what ideas or feedback you have for us for the next event.
We are extremely excited to get started on the next event and want to incorporate ideas from our community. Our entire user developer ecosystem now revolves around the IPinfo community, so if you have any ideas to share about the next IPinfo IP Hunt or want to know when the next hunt will start, join the IPinfo community today.
